Content Protection
Content protection schemes supported by the plugin are summarised as:
Windows Desktop
Custom HTTP header fields can be specified which can help with server side validation (requires using the WinRT API). This is only supported for adaptive media (HLS/DASH).
HLS with AES-128 clear-key, direct key and key request is supported
Android
Custom HTTP header fields can be specified which can help with server side validation
HLS with AES-128 clear-key, direct key and key request is supported (make sure your TS segments are 188 bytes aligned for maximum Android compatibility)
A file offset feature allows you to access files hidden within a file at an offset.
macOS / iOS / tvOS
HLS with AES-128 clear-key, direct key and key request using an auth token in the HTTP header (“Authorization” field). More information about HLS encryption can be read in the RFC here: https://tools.ietf.org/html/draft-pantos-http-live-streaming-23
Custom HTTP header fields can be specified which can help with server side validation
Note
DRM schemes Fairplay, Widevine, PlayReady etc are not yet supported
File Offset
On Android (this is the only platform that currently supports this feature) in the Core Edition a file offset (in bytes) can be specified which allows loading of media which is embedded within another file. This is very useful for hiding media.
In Windows you can use the following command via the command-line to easily append your video to a dummy file:
copy /b DummyFile.dat + MyVideo.mp4 MysteryFile.dat
The offset can be set via the UI in the Platform Specific > Android section, or via PlatformOptionsAndroid in scripting:
// Set the Android file offset to 54321 bytes (the size of the dummy file, or the offset into a file if you have as embedding it within a file)
mediaPlayer.PlatformOptionsAndroid.fileOffset = 54321;
An alternative is to use a dummy video file, and then append your real media to this file, as this will then allow the dummy video to play instead of your real media, making it not obvious that you're hiding your video.
In Windows you can use the following command via the command-line to easily append your video to a dummy video:
copy /b DummyVideo.mp4 + MyVideo.mp4 MysteryFile.mp4
In Windows you can use the following command to create a batch file for converting multiple files easily:
copy /b DummyVideo.mp4 + %1 %~n1-hidden.mp4
Custom HTTP Headers
Custom HTTP headers can be specified in the Ultra Edition. Typically we have seen them used for authentication, token exchange and cookies. Here are Some examples of formats we’ve used in the past:
For authentication the typical HTTP headers are:
Authorization Basic <username>:<password>
Authorization Bearer <token>
For cookies the typical HTTP headers are:
Cookie <cookie-name>=<cookie-value>;<cookie-name2>=<cookie-value2>;
Note
On Windows custom HTTP headers are only supported on the WinRT API, and are only supported for adaptive media (HLS and DASH).
Note
On Android custom HTTP headers are only supported on the ExoPlayer API, the MediaPlayer API doesn't support this.
In the plugin custom headers can be specified via the component UI or via script. Using the component UI you would specify them like:

Note
The fields will turn red in the editor if the format is not correct
Or via scripting:
// On Windows the Video API needs to be set to WinRT to use custom HTTP headers
mediaPlayer.PlatformOptionsWindows.videoApi = Windows.VideoApi.WinRT;
// Set custom HTTP headers on Android platform
mediaPlayer.PlatformOptionsAndroid.httpHeaders.Add("Authorization", "Bearer <token>");
mediaPlayer.PlatformOptionsAndroid.httpHeaders.Add("Cookie", "<cookie-name>=<cookie-value>;<cookie-name2>=<cookie-value2>;");
// For Basic Authorization the <username>:<password> should be base64 encoded:
string username = "user";
string password = "password";
string base64token = System.Convert.ToBase64String(System.Text.Encoding.UTF8.GetBytes(username + ":" + password));
mediaPlayer.PlatformOptionsAndroid.httpHeaders.Add("Authorization", "Basic " + base64token);
// Set custom HTTP headers on the currently running platform
mediaPlayer.GetCurrentPlatformOptions().httpHeaders.Add("MyHlsUriToken", "1234567890");
Note
Basic Authorization headers don't appear to work when using WinRT and RTSP streams
Note
Internally custom HTTP headers are passed in this string format: name1:value1\r\nname2:value2
HLS AES-128 Encrypted Playback
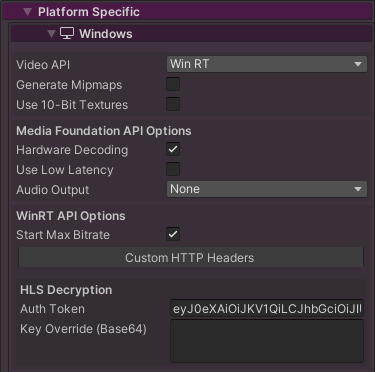
In the Ultra Edition AES-128 HLS streams are supported. This allows playback of encrypted content with secure key exchange. There is support on macOS, iOS, tvOS, Android (only using Exoplayer API) and Windows (only using WinRT API).
Key retrieval from a server URL usually requires an authentication token, which can be specified using the member keyServerToken), or this can be ignored if your key retrieval server doesn’t require any token for key retrieval (clear-key). The auth token is a string that is inserted into the “Authorization” HTTP field when retrieving the decryption key from the server URL specified in the HLS manifest. Sometimes this field has the "Bearer" prefix.
We also added some functionality to specify the decryption key data directly. overrideDecryptionKey can be used to specify the key directly as an array of bytes. Using this will bypass any server key retrieval, which can be useful for debugging.
Scripting examples:
// On Windows the Video API needs to be set to WinRT to use AES-128 keys
mediaPlayer.PlatformOptionsWindows.videoApi = Windows.VideoApi.WinRT;
// Set the authentication token for the key server to allow access of the decryption key for iOS platform
mediaPlayer.PlatformOptionsIOS.keyAuth.keyServerToken = "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1cm46bWljcm9zb2Z0OmF6dXJlOm1lZGlhc2VydmljZXM6Y29udGVudGtleWlkZW50aWZpZXIiOiI5ZGRhMGJjYy01NmZiLTQxNDMtOWQzMi0zYWI5Y2M2ZWE4MGIiLCJpc3MiOiJodHRwOi8vdGVzdGFjcy5jb20vIiwiYXVkIjoidXJuOnRlc3QiLCJleHAiOjE3MTA4MDczODl9.lJXm5hmkp5ArRIAHqVJGefW2bcTzd91iZphoKDwa6w8");
// Just specify a decryption key manually for iOS platform
mediaPlayer.PlatformOptionsIOS.keyAuth.overrideDecryptionKey = new byte[] { 12, 95, 93, 64, 234, 76, 93, 64, 125, 0, 95, 23 };
// Just specify a decryption key manually using base64 for Windows platform
mediaPlayer.PlatformOptionsWindows.keyAuth.overrideDecryptionKey = Convert.FromBase64String(base64Key);
// Just specify a decryption key manually loading from a 16 byte .key file for Windows platform
mediaPlayer.PlatformOptionsWindows.keyAuth.overrideDecryptionKey = System.IO.File.ReadAllBytes("C:/myfile.key");
These options can also be specified in the MediaPlayer inspector UI (in the Platform Specific section) under HLS Decryption: